Few countries maintain tighter control than North Korea. Inside its borders, the government built a surveillance system that penetrates everyday life. Authorities monitor behavior and design the entire digital environment to limit independent action. Phones, computers, and even radios operate within strict boundaries.
The goal is to shape how people communicate, think, and even interact with each other.
Controlled Internet

North Koreans use a national intranet called Kwangmyong, not the global internet. This closed system hosts only state-approved websites and offers no access to international platforms. It prevents exposure to external news, uncensored history, or independent thought. By controlling what citizens read and watch, the regime keeps the population disconnected from ideas that might challenge its authority.
Ideological Autocorrect

What happens when you type words the government doesn’t like? They’re automatically replaced. The system changes “South Korea” to “puppet state,” “United States” to “imperialist enemy,” and “oppa” to “comrade.” Residents using everyday slang or neutral geographic terms see them replaced with state-approved propaganda.
Keyword Monitoring
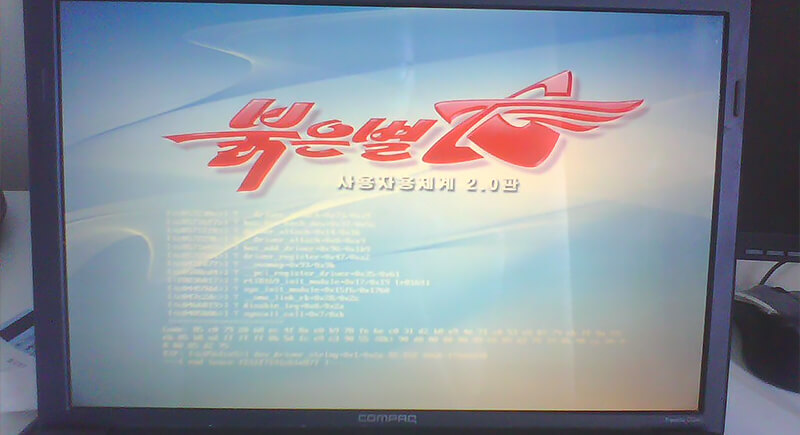
The control doesn’t stop at autocorrect. North Korea’s Red Star operating system also scans documents and deletes forbidden words. When users write documents, the system checks for phrases the regime dislikes. These might include criticisms of the government or mentions of other countries’ leaders. Files with banned words are deleted automatically.
Phone Surveillance

Every mobile phone sold in the country comes with detection tools installed by default. The software automatically takes screenshots and sends them to central servers. It also logs which apps you use and when. Words that don’t match official messaging get flagged or autocorrected.
Hardware Locks

To hear outside news, like from South Korea or China, individuals have to physically tamper with their devices. Radios and televisions are built to receive only approved frequencies and lock out anything the state hasn’t sanctioned. To circumvent this, individuals must make illegal hardware changes, which the government treats as a serious offense.
Forced Updates

Government-issued software searches for banned content. Updates automatically scan devices for non-native media files, especially TV shows and movies. When they detect something unauthorized, they remove it without notice. South Korean dramas and international films are frequent targets. To avoid punishment, users often erase media on their own.
Signal Scanning

As the country’s digital watchdog, Bureau 27 provides its agents with portable devices that detect illegal mobile signals, especially in regions near the Chinese border. These scanners blink when they locate a foreign frequency and prompt immediate investigations. One witness described agents with blinking red antennae arresting her after tracing her call.
Call Penalties

The risks of using a banned phone are extreme. Anyone caught making international calls without government permission can face a prison sentence or forced labor. Even if the call is personal, like checking in with a relative, it’s treated as espionage. Stories circulate about people disappearing after one conversation. This level of punishment keeps most citizens too afraid to even attempt a call.
Bluetooth Policing

Without access to the internet, many citizens share content using USB drives and Bluetooth. These devices carry TV shows, books, and songs passed between friends, but the authorities make sure to watch this activity closely. During random inspections, officials check phones and laptops for unauthorized files.
Informant Culture

The regime doesn’t rely on technology alone. It also builds networks of informants who report suspicious behavior. These informants can be neighbors, coworkers, or even family members. People become hesitant to speak freely, even at home. A harmless joke or private complaint can end up in an official file.
Device Inspections

Random searches of personal electronics are a routine tactic used by state security forces. Officials inspect phones, computers, and even storage devices for banned content or unauthorized modifications. As a result, many delete files after a single use or avoid storing anything that could be seen as suspicious.
Usage Logs

Digital devices track far more than citizens realize. Every app launch, message, and screen interaction is recorded. Time stamps and location data are automatically compiled into detailed usage logs. This information helps authorities identify behavioral patterns and detect changes that might signal dissent.
Digital Traps

Security forces sometimes distribute files that appear to be foreign films, songs, or political leaflets. These bait materials are seeded on USB sticks or shared via Bluetooth. When opened, the file alerts authorities and log the identity of the user or their device. People who access these traps are flagged for further investigation or immediate arrest.
School Indoctrination

From an early age, children are taught to idolize the regime and report disloyalty, even within their own families. School programs emphasize surveillance as a civic duty. Students are encouraged to inform teachers about conversations or actions that suggest unrest.
Neighborhood Watch

Each community has an inminban, or neighborhood unit, led by a resident appointed by local authorities. These leaders track household activities, report suspicious behavior, and detect compliance with government rules. If anyone is found violating any, they are handed out punishments that usually involve humiliation in front of neighbors.